CDPHP
Multi-factor authentication
About the Project
This project came about as part of a conversation with stakeholders and potential security improvements within our product.
My Role: Lead UX Designer
Project Duration: 3 Weeks
Problem: All of the portals (Member, Employer, Broker and Provider) contain sensitive healthcare related information that, per HIPAA, must be protected. An additional layer of security should be implemented in conjunction with the standard login credentials.
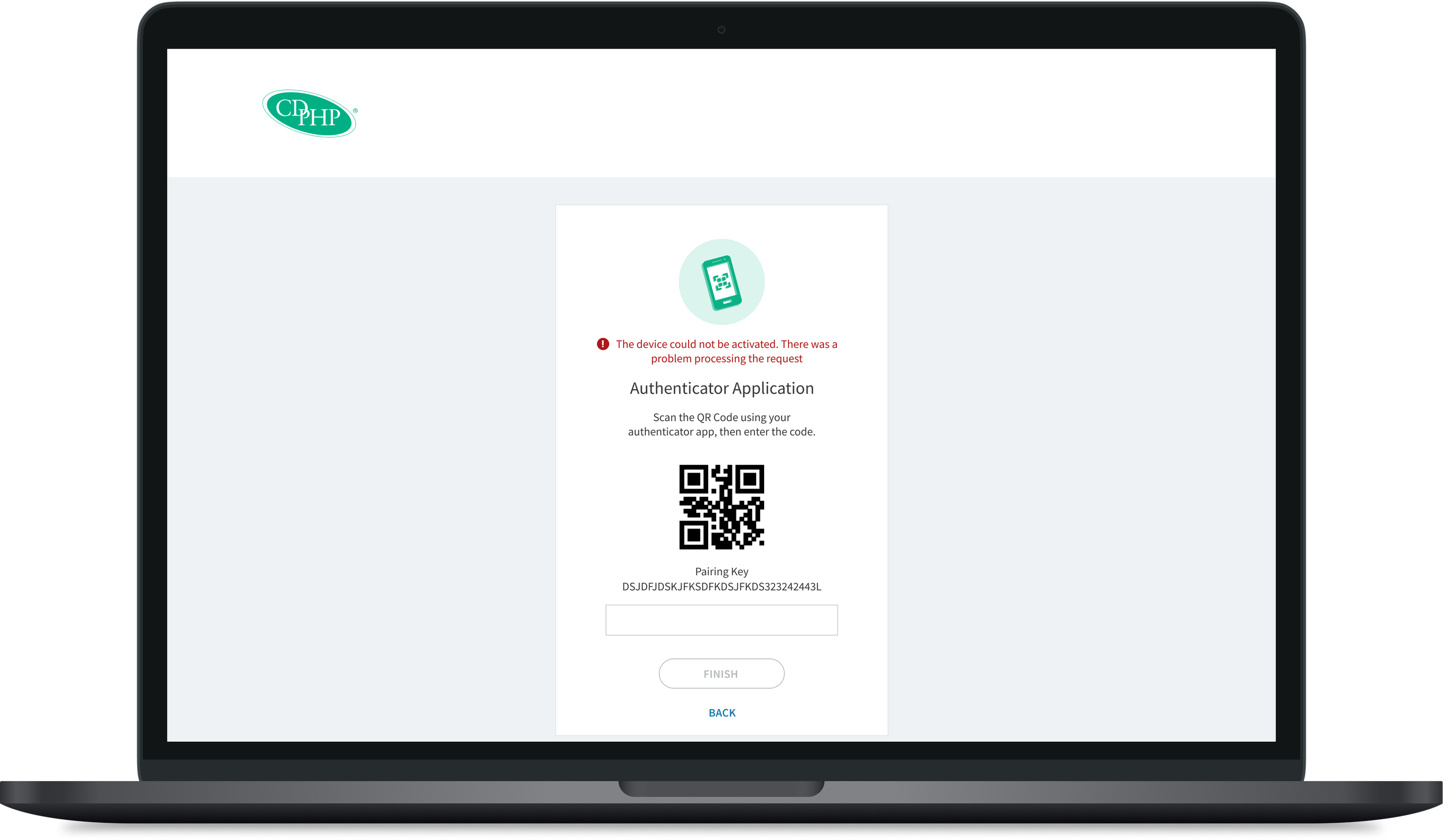
Solution Overview: Multi-factor Authentication using different authentication methods was implemented in order to help secure user logins.
Ideation
Since the conceptualized solution to our problem was evident from the very first conversation, rather than spend a ton of time on research, I worked quickly toward the ideation phase.
Working pen to paper, I was able to identify rough requirements, sketch out some flow designs and finally mapped out an appropriate user flow. These initial brainstorming sessions set the tone for the rest of project. The better the foundation, the easier the designs would come to fruition.
User Flow
UI Design
By establishing the user flow during ideation, then working through some low fidelity sketches and wireframes, I was able to apply our brand to the final high fidelity designs. As the user flow model was more pertinent to this project than a working prototype, the Figma designs were left in a static state.
Taking into account 4 user portals, a responsive design, and a mobile app required many screens to be mocked up for both stakeholders and engineering teams to understand the full scope. These consisted of, but were not limited to:
Registration
Sign in methods
Errors
Password reset
The aforementioned 4 portals and app
Responsive layouts for desktop, tablet and mobile
Takeaways
This multi-factor authentication project seemed to be a huge undertaking given the time constraints. Getting the chance to really brainstorm a thorough flow that would account for our end-user's needs was an invaluable learning experience. Accounting for the various entry points that would lead an user to their login destination required a lot of scribbles, iterations, coffee and patience. Overall, we accomplished the task at hand and paved the way for future improvements to protect our user's data.